SocGholish Malware Campaign Infiltrates Major News Sites To Infect PCs

Threat researchers at the cybersecurity firm Proofpoint have discovered an extensive malware campaign targeting readers of online news outlets. A threat actor tracked as TA569, also known as SocGholish, has managed to compromise the infrastructure of a media company that serves content to a large number of news publications. Proofpoint researchers have found SocGholish injecting malicious code into the Javascript codebase that pushes the company’s content to partnering news sites. Visitors to these sites may end up accidentally installing malware if they aren’t careful.
Proofpoint has yet to reveal the name of the compromised media company, but has said that the company serves both video and advertising content to online news publications. According to the cybersecurity firm, “[m]ore than 250 regional/national newspaper sites have accessed the malicious Javascript. The actual number of impacted hosts is known only by the impacted media company.”
Proofpoint has yet to reveal the name of the compromised media company, but has said that the company serves both video and advertising content to online news publications. According to the cybersecurity firm, “[m]ore than 250 regional/national newspaper sites have accessed the malicious Javascript. The actual number of impacted hosts is known only by the impacted media company.”
SocGholish has been running similar malware campaigns since at least 2019, and past behavior has shown that once the threat actor gains unauthorized access to a Javascript codebase, it frequently injects, removes, and re-injects updated malicious code. This pattern of behavior can make the malware hard to detect, as it doesn’t impact website visitors in a consistent manner. Intermittent reports of differing malicious behavior can be mistakenly dismissed as problems on the user end, particularly when a search of the offending Javascript codebase turns up nothing on account of the malicious code being removed by the threat actor.
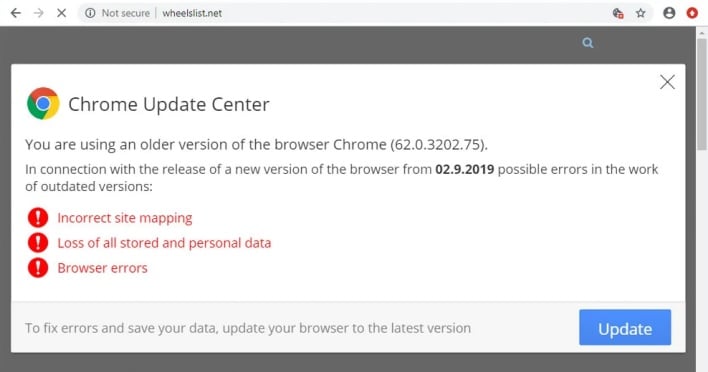
However, while they may vary in appearance, fake browser updates are a running theme for the malware pushed by SocGholish. Visitors to affected websites may be met by notifications rendered in the browser window advising them to update to the latest version of whatever browser is in use. However, rather than performing a regular browser update within the application or the operating system’s package manager, the update button instead downloads a zip file containing a malicious payload. The file is usually named [Browser].Updater.zip, prompting users to open the file and unknowingly release whatever malware is contained within. Users should be wary of browser updates that don’t follow the usual update process, so as to avoid unpacking a nasty malware surprise.
However, while they may vary in appearance, fake browser updates are a running theme for the malware pushed by SocGholish. Visitors to affected websites may be met by notifications rendered in the browser window advising them to update to the latest version of whatever browser is in use. However, rather than performing a regular browser update within the application or the operating system’s package manager, the update button instead downloads a zip file containing a malicious payload. The file is usually named [Browser].Updater.zip, prompting users to open the file and unknowingly release whatever malware is contained within. Users should be wary of browser updates that don’t follow the usual update process, so as to avoid unpacking a nasty malware surprise.

