TeamTNT Deploys Kangaroo Malware Attack On Bitcoin Targeted At Breaking Encryption

Researchers at Aqua Security have discovered cyberattacks that appear to have been conducted by TeamTNT, a threat actor previously thought to be defunct. The researchers encountered three different attacks, each of which looks to be new. One of these attacks, which the researchers have dubbed the “Kangaroo attack,” is notable for leveraging distributed computing power in an attempt to break the encryption that underlies bitcoin.
TeamTNT was a threat actor highly skilled at compromising cloud environments. The threat actor’s attacks made use of never-seen-before techniques and exploits, as TeamTNT developed its own toolbox, rather than relying on the same methods used by many other threat actors. After operating in this manner for almost two years, TeamTNT called it quits in November 2021. The threat actor subsequently ceased to develop and deploy new malware. That said, the threat actor did not take down its infrastructure, leaving its extant malware to continue its spread.
TeamTNT was a threat actor highly skilled at compromising cloud environments. The threat actor’s attacks made use of never-seen-before techniques and exploits, as TeamTNT developed its own toolbox, rather than relying on the same methods used by many other threat actors. After operating in this manner for almost two years, TeamTNT called it quits in November 2021. The threat actor subsequently ceased to develop and deploy new malware. That said, the threat actor did not take down its infrastructure, leaving its extant malware to continue its spread.
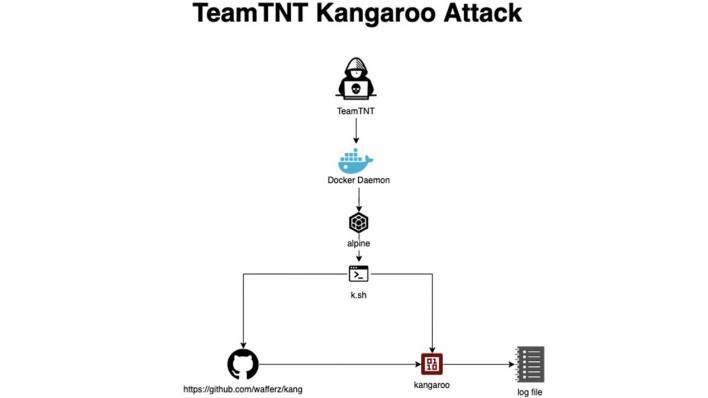
Now, almost a year after TeamTNT announced its retirement, three new malware campaigns point to TeamTNT as the originator. Two of these attacks, the Kangaroo attack and the What Will Be attack, target misconfigured Docker Daemons and install Alpine Linux container images that download and run malicious shell scripts. The script run in the What Will Be attack exploits a vulnerability to escape the image and compromise the host. Further shell scripts then schedule cron jobs and install rootkits and cryptominers. The third attack, dubbed Cronb, is not completely new, but uses new C2 server addresses compared to previous attacks. It is used for lateral access across a network, persistence, and to install rootkits and cyptominers like What Will Be.
However, while the two other attacks infect victims’ systems to mine cryptocurrency, the Kangaroo attack does something of the opposite. It leverages infected environments to run a solver algorithm intended to break the SECP256K1 encryption that underlies Bitcoin. Breaking this encryption with today’s computers is considered to be a virtually impossible task, but the Kangaroo attack is tasking compromised environments with doing so anyway. The solver algorithm splits the job up into smaller tasks, enabling TeamTNT to potentially leverage a lot of stolen computer power simultaneously by distributing different chunks to each system compromised by the attack. Even so, breaking Bitcoin’s encryption in this way is still highly unlikely, making this particular attack seem somewhat strange. It's not clear what the motive or intention is behind this particular attack.
However, while the two other attacks infect victims’ systems to mine cryptocurrency, the Kangaroo attack does something of the opposite. It leverages infected environments to run a solver algorithm intended to break the SECP256K1 encryption that underlies Bitcoin. Breaking this encryption with today’s computers is considered to be a virtually impossible task, but the Kangaroo attack is tasking compromised environments with doing so anyway. The solver algorithm splits the job up into smaller tasks, enabling TeamTNT to potentially leverage a lot of stolen computer power simultaneously by distributing different chunks to each system compromised by the attack. Even so, breaking Bitcoin’s encryption in this way is still highly unlikely, making this particular attack seem somewhat strange. It's not clear what the motive or intention is behind this particular attack.

