Sneaky Chameleon Banking Malware Defeats Biometric Security On Android, Steals PINs
When Chameleon first popped up, it posed as crypto, banking, and government apps. Now, the malware uses the Zombinder service, which attaches malicious apps to legitimate ones. The user believes they've installed a particular app, and it appears to work normally, but the malware comes along for the ride. The creators of Zombinder claim the sidecar virus is undetectable by Google Protect security and Chameleon is using this platform to pose as Google Chrome.
The other new twist for Chameleon is the way it tries to gain deeper access to the system. Android's Accessibility service allows trusted apps to emulate buttons, control the screen, or disable features to help disabled individuals use their phones more efficiently. However, the capabilities granted through Accessibility can also be used to compromise the device, so Google has clamped down on how devs can use these APIs. Apps can't just flip the Accessibility switch on their own. It's a multistep process, so the updated Chameleon malware has added an HTML pop-over that guides the user through the steps. Because the malware is hiding behind a legitimate app (in this case Chrome), the user might not know anything is amiss.
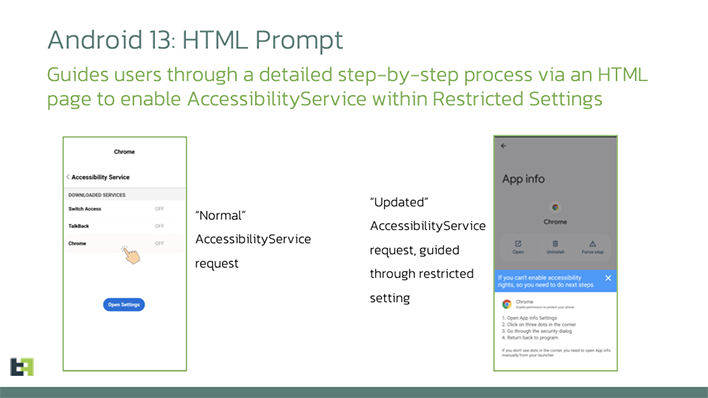
When Chameleon has Accessibility control, it will disable the biometric unlock method. As soon as the user unlocks their device with a PIN or password, the malware records it for later use. The malware can then wake up at any time and unlock the device to upload stolen personal information and login data.
Chameleon has also gained support for Android's AlarmManager API, which gives apps the ability to wake up in the background to run tasks. The malware can adjust its behavior based on the computing environment and Accessibility status. According to ThreatFabric, which has examined the new Chameleon variant, the best way to stay safe is to keep your phone's Google Protect features enabled and only get apps from official sources. Chameleon is being distributed through third-party app repositories, hacked web pages, and Discord.

