MooBot Mirai Botnet Gives Hackers Complete Control Of Your D-Link Router, Update ASAP

Cybersecurity researchers from Palo Alto Networks’ Unit 42 have discovered a campaign exploiting multiple vulnerabilities in D-Link routers to spread botnet malware. A botnet is a network of compromised consumer or enterprise devices controlled by a threat actor to carry out malicious tasks, such as mining cryptocurrency without the knowledge of the devices’ owners or conducting a distributed denial-of-service (DDoS) attack. Some botnets are thousands of devices strong and possess the ability to bombard services with millions of requests per second.
Since Wi-Fi routers interface directly with the open web, they make for prime targets for threat actors looking to build out a botnet. The campaign detailed by Unit 42 researchers leverages four different vulnerabilities spread across various D-Link routers. All four vulnerabilities are listed in the National Vulnerability Database (NVD), and three of them have critical severity ratings of 9.8 out of 10.
The fourth vulnerability, which is listed as CVE-2015-2051 and affects D-Link’s DIR-645 Router, currently lacks a CVSS Version 3.x severity score as it was recently updated with additional information and is awaiting reanalysis. However, unlike the other three vulnerabilities, this one is listed in the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities Catalog. While D-Link has released patches for all four vulnerabilities exploited in this campaign, the DIR-645 Router has reached end of life, so CISA recommends retiring this device.
Since Wi-Fi routers interface directly with the open web, they make for prime targets for threat actors looking to build out a botnet. The campaign detailed by Unit 42 researchers leverages four different vulnerabilities spread across various D-Link routers. All four vulnerabilities are listed in the National Vulnerability Database (NVD), and three of them have critical severity ratings of 9.8 out of 10.
The fourth vulnerability, which is listed as CVE-2015-2051 and affects D-Link’s DIR-645 Router, currently lacks a CVSS Version 3.x severity score as it was recently updated with additional information and is awaiting reanalysis. However, unlike the other three vulnerabilities, this one is listed in the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities Catalog. While D-Link has released patches for all four vulnerabilities exploited in this campaign, the DIR-645 Router has reached end of life, so CISA recommends retiring this device.
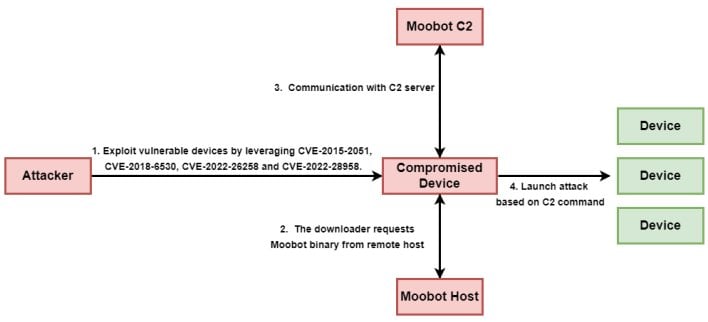
Attackers can exploit all four of the vulnerabilities leveraged in this campaign to remotely execute code without authorization. The threat actors behind the campaign make use of this capability to direct affected routers to download a MooBot malware payload. MooBot is a variant of the Mirai botnet malware that was first discovered back in December of last year. Once the malicious payload infects the compromised routers, the routers join the larger MooBot network by initiating communication with the MooBot command-and-control (C2) server. The threat actors controlling the C2 server can then direct the compromised routers to conduct DDoS attacks on targeted servers and services.
Those with D-Link routers should make sure these devices are up to date, so as to protect them from being subsumed into the MooBot botnet. The four vulnerabilities leveraged in this campaign are as follows:
Those with D-Link routers should make sure these devices are up to date, so as to protect them from being subsumed into the MooBot botnet. The four vulnerabilities leveraged in this campaign are as follows:
| Vulnerability | Affected Router(s) |
| CVE-2015-2051 |
DIR-645 |
| CVE-2018-6530 | DIR-880L, DIR-868L, DIR-65L, DIR-860L |
| CVE-2022-26258 |
DIR-816L |
| CVE-2022-28958 |
DIR-820L |

