LEGO Fixes Startling BrickLink Exploit That Could Allow Hackers To Hijack Accounts

Back in October, a researcher at the cybersecurity firm Salt Security uncovered multiple security vulnerabilities in the LEGO BrickLink website that could have allowed hackers to hijack users’ accounts and arbitrarily read files on the the Amazon cloud server hosting the website. Upon making this discovery, the researcher promptly disclosed the vulnerabilities to the LEGO security team, which confirmed the presence of the vulnerabilities. LEGO then updated the BrickLink website to fix these vulnerabilities in early November, with Salt Labs providing confirmation that the vulnerabilities were no longer exploitable.
BrickLink is a popular online marketplace for buying and selling second-hand LEGO bricks, mini-figures, and whole sets. BrickLink boasts over a million registered members and came under the LEGO Group’s ownership in 2019. It’s fortunate that the LEGO security team was quick to respond to Salt Security’s vulnerability disclosure, as the website’s relatively large user-base could make it a target for threat actors.
BrickLink is a popular online marketplace for buying and selling second-hand LEGO bricks, mini-figures, and whole sets. BrickLink boasts over a million registered members and came under the LEGO Group’s ownership in 2019. It’s fortunate that the LEGO security team was quick to respond to Salt Security’s vulnerability disclosure, as the website’s relatively large user-base could make it a target for threat actors.
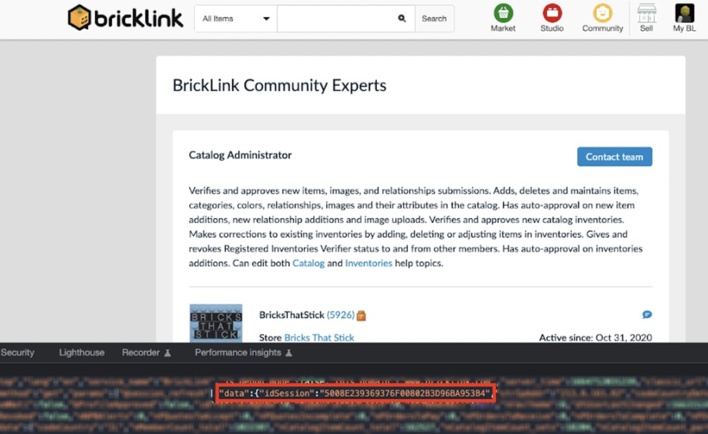
The first vulnerability disclosed by Salt Labs concerned code injection. The BrickLink website contained a coupon search box that would accept any entered text and render it into the webpage’s HTML. The researcher was able to leverage this behavior to inject JavaScript into BrickLink webpages. The researcher then found a webpage on the site that stored the current user’s session ID value in the page’s code.
Using this knowledge, the researcher created a JavaScript payload that, when injected into the webpage, would steal the unprotected session ID and send it to a server controlled by the researcher. A threat actor could have abused this exploit to hijack users’ accounts by directing people to the BrickLink website with a carefully crafted link that injected the stealer payload.
Using this knowledge, the researcher created a JavaScript payload that, when injected into the webpage, would steal the unprotected session ID and send it to a server controlled by the researcher. A threat actor could have abused this exploit to hijack users’ accounts by directing people to the BrickLink website with a carefully crafted link that injected the stealer payload.
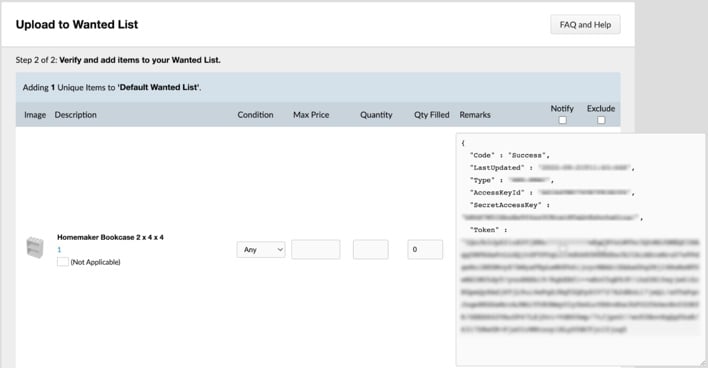
The researcher also discovered a vulnerability in BrickLink’s “Wanted List.” This wish list feature accepted and processed XML input in a way that allowed for successful XML External Entities (XXE) injection attacks. By entering specific XML input, the researcher was able to instruct the server to respond by revealing the contents of files stored on the server.
The researcher then determined that the server hosting the BrickLink website running on Amazon Web Services (AWS) Elastic Compute Cloud (EC2). Armed with this knowledge and the arbitrary file read exploit, the researcher the directed the server to reveal its AWS EC2 credentials. The server complied, handing over credentials that could facilitate unauthorized access to BrickLink’s internal servers. Thankfully, rather than abusing these credentials, the researcher reported the vulnerabilities to the LEGO security team so they could be fixed.
The researcher then determined that the server hosting the BrickLink website running on Amazon Web Services (AWS) Elastic Compute Cloud (EC2). Armed with this knowledge and the arbitrary file read exploit, the researcher the directed the server to reveal its AWS EC2 credentials. The server complied, handing over credentials that could facilitate unauthorized access to BrickLink’s internal servers. Thankfully, rather than abusing these credentials, the researcher reported the vulnerabilities to the LEGO security team so they could be fixed.