Iranian Hackers Use An Old Browser Trick To Steal Google Gmail User Data Undetected

Charming Kitten is known for targeting individuals that find themselves at odds with the Iranian regime. One of its tactics was to use a tool called HYPERSCRAPE to steal data from victim’s email accounts. HYPERSCRAPE – not to be confused with Ubisoft's Hyper Scape – was first detected in 2021 by Google’s Threat Analysis Group (TAG) and evidence of its use dates back to 2020. TAG has now released a breakdown of how the tool operated.
HYPERSCRAPE is a relatively simple .NET application which acts as a follow-on tool once a user’s account has already been compromised. Attackers need to either obtain a victim’s credentials through other means or hijack an authenticated session first. HYPERSCRAPE is then used to download the contents of an inbox without any sign to the victim that something is amiss. It has been used against Gmail, Yahoo!, and Outlook accounts, but only its method against Gmail is detailed in the writeup.
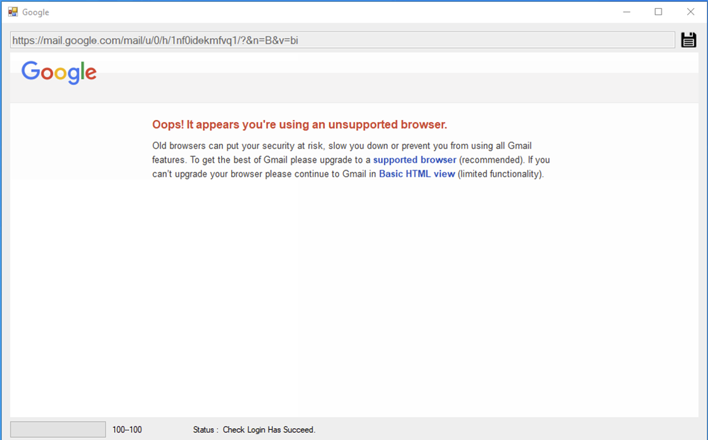
HYPERSCRAPE first tricks Gmail into displaying the basic HTML view instead of using its new enhanced interface. It accomplishes this by setting its User Agent to display as an outdated browser. HTML view allows the tool to directly parse emails. After logging in, HYPERSCRAPE temporarily changes the inbox’s language to English.
The tool then downloads each email in the account one by one. If an email was previously unread, the tool takes care to mark it as unread after downloading. Once finished, the tool reverts the settings it changed and deletes all security notices from Google which leaves the victim none-the-wiser. Accounts can remain compromised indefinitely for continued surveillance.
TAG reports that HYPERSCRAPE has been effectively deployed against fewer than two dozen accounts within Iran due to Charming Kitten’s very selective targeting. Nevertheless, the prospect of a complete and largely automated information dump is very concerning. Other parties could leverage similar tactics for espionage, extortion, suppression, or worse at a broader scale. It also goes to show how modernized defenses can be effectively side-stepped as long as legacy functions are in place.
Google’s TAG does not disclose any particular measures taken to prevent this attack from working in the future. HTML view is still an essential fallback function for many users around the world. Instead, TAG recommends that high-risk users who may be targeted in such an attack should leverage Google’s Advanced Protection Program and Account Level Enhanced Safe Browsing to increase their defensive posture.
Top Image Credit - Ashutosh Sonwani on Pexels