Delete These Malware-Laden Google Chrome Extensions With 1.4M Collective Downloads Now

We frequently write about Android malware smuggled onto the Google Play Store in the form of what appear to be legitimate apps. However, the Play Store isn’t the only Google-run app store with a malware problem. A new report by McAfee Labs identifies five extensions on the Chrome Web Store that contain malicious payloads. These malware-laden extensions together have an alarming 1.4 million downloads.
The five extensions all exhibit the same malicious behavior. Once installed, these extensions begin logging every site visited by the user and sending that information to servers controlled by a threat actor. The command-and-control (C2) servers check each website against a list of online marketplaces for which the threat actor has registered an affiliate ID. If the user visits a site on this list, the browser extensions inject code into the website, modifying the browser cookies to include the threat actor’s affiliate code for that site. In the event the user makes a purchase on this e-commerce site, the threat actor receives an affiliate payment for the purchase.
The five extensions all exhibit the same malicious behavior. Once installed, these extensions begin logging every site visited by the user and sending that information to servers controlled by a threat actor. The command-and-control (C2) servers check each website against a list of online marketplaces for which the threat actor has registered an affiliate ID. If the user visits a site on this list, the browser extensions inject code into the website, modifying the browser cookies to include the threat actor’s affiliate code for that site. In the event the user makes a purchase on this e-commerce site, the threat actor receives an affiliate payment for the purchase.
These extensions pose a privacy and security threat that extends beyond just malicious code injection. Besides receiving unearned affiliate payments, the threat actor behind these extensions is able to observe victims’ browser behavior along with some identifying information. Each time a user visits a new URL, the extensions send a report to the C2 servers which includes not just the URL but also the country, city, and zip code of the user’s device and a unique user ID. The threat actor could use this information to identify victims and track their browsing habits.
The extensions mask their malicious behavior by performing their advertised functions as users expect them to do. This helps explain why the extensions have so many downloads. Some of the extensions also wait fifteen days before beginning to report browser activity to the C2 servers to further evade suspicion. Google has removed these extensions from the Chrome Web Store, but users who already installed the extensions will still have to delete them from their browsers.
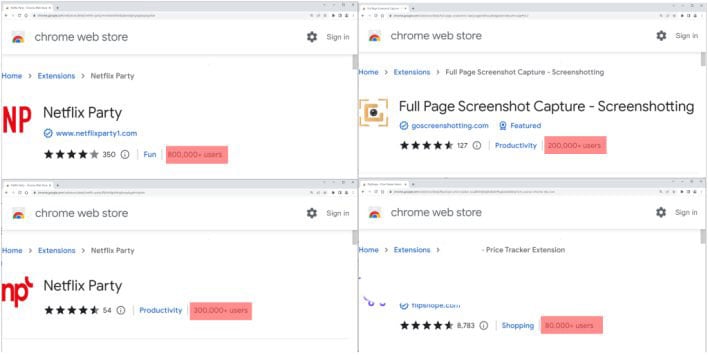
The five malicious extensions are as follows:
The extensions mask their malicious behavior by performing their advertised functions as users expect them to do. This helps explain why the extensions have so many downloads. Some of the extensions also wait fifteen days before beginning to report browser activity to the C2 servers to further evade suspicion. Google has removed these extensions from the Chrome Web Store, but users who already installed the extensions will still have to delete them from their browsers.
The five malicious extensions are as follows:
| Name |
Extension ID |
Downloads |
| Netflix Party |
mmnbenehknklpbendgmgngeaignppnbe | 800,000 |
| Netflix Party 2 |
flijfnhifgdcbhglkneplegafminjnhn |
300,000 |
| Full Page Screenshot Capture – Screenshotting |
pojgkmkfincpdkdgjepkmdekcahmckjp |
200,000 |
| AutoBuy Flash Sales |
gbnahglfafmhaehbdmjedfhdmimjcbed | 20,000 |

