Heads-Up, These Are The Apps Malware Authors Most Often Impersonate

Malware campaigns employ different techniques to smuggle malicious software onto computing devices without the notice of users or anti-virus systems. Threat actors who develop and distribute malware frequently rely on various forms of mimicry to take advantage of users’ trust in legitimate websites, services, and applications. Phishing attacks can direct users to download pages that appear to be part of familiar and trusted websites, but actually distribute trojans designed to look like popular apps.
VirusTotal, an online service that analyzes over two million files and websites a day by checking them against over seventy anti-virus scanners and domain block lists, has released a report providing insight into the various methods of deception employed in malware campaigns. According to the report, threat actors are increasingly packaging malware with legitimate app installers, as well as designing malware to visually mimic legitimate applications.
VirusTotal, an online service that analyzes over two million files and websites a day by checking them against over seventy anti-virus scanners and domain block lists, has released a report providing insight into the various methods of deception employed in malware campaigns. According to the report, threat actors are increasingly packaging malware with legitimate app installers, as well as designing malware to visually mimic legitimate applications.
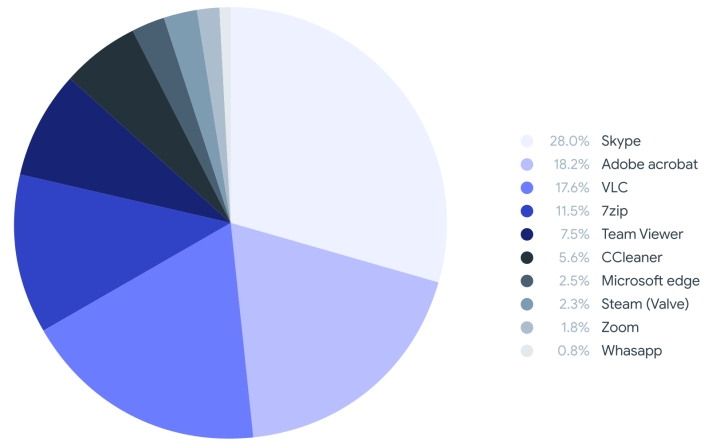
One of the methods threat actors are increasingly using to make malware appear legitimate is making the program icons identical or visually similar to those of popular apps. VirusTotal found that the Skype, Adobe Acrobat, and VLC icons were the program icons most frequently mimicked by malicious Windows software between January 2021 and July 2022. The report also discusses malicious installers that package malware with actual installers for popular software. VirusTotal names Google Chrome, Malwarebytes, Windows Update, Zoom, Brave, Firefox, ProtonVPN, and Telegram as popular apps threat actors like to package with malware.
VirusTotal was surprised to find how frequently malicious files are signed with stolen signing keys. Earlier this year, a group of hackers known as LAPSUS$ claimed to steal 1TB of data from NVIDIA. The group publicly leaked only 20GB of this data before the seven members of the group were arrested. Nonetheless, this leak still caused significant damage as it revealed two of NVIDIA’s code signing certificates, which malware developers promptly began using to sign malicious packages. NVIDIA is not unique in having its signing keys stolen. Other companies have had their certificates stolen as well. Some of these stolen keys become invalidated, whether by expiring or being revoked. However, VirusTotal still detected almost one million malicious files signed with valid certificates between January 2021 and June 2022.
VirusTotal was surprised to find how frequently malicious files are signed with stolen signing keys. Earlier this year, a group of hackers known as LAPSUS$ claimed to steal 1TB of data from NVIDIA. The group publicly leaked only 20GB of this data before the seven members of the group were arrested. Nonetheless, this leak still caused significant damage as it revealed two of NVIDIA’s code signing certificates, which malware developers promptly began using to sign malicious packages. NVIDIA is not unique in having its signing keys stolen. Other companies have had their certificates stolen as well. Some of these stolen keys become invalidated, whether by expiring or being revoked. However, VirusTotal still detected almost one million malicious files signed with valid certificates between January 2021 and June 2022.
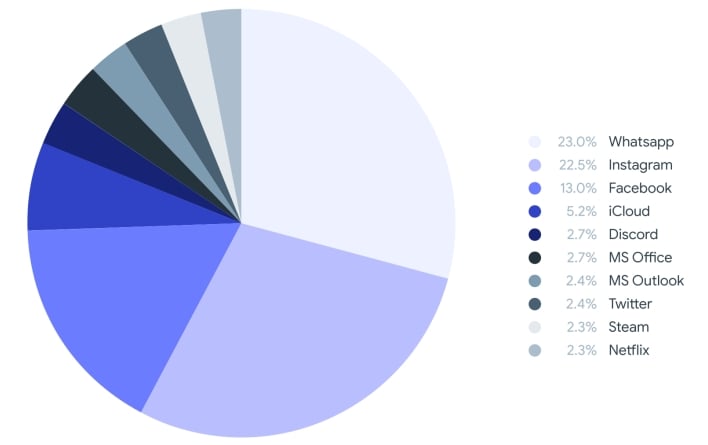
Lastly, VirusTotal looked not just at malware packages themselves, but also websites that distribute malware. As mentioned above, phishing attacks often employ websites designed to look like legitimate websites. Fraudulent websites often use the same favicon as that of the websites they mimic. A favicon is the little icon that appears at the top of a web browser when you visit a website. According to the report, the Whatsapp, Instagram, and Facebook favicons are those most frequently used by malicious websites.

