Millions Of Home Wi-Fi Routers Are Likely Vulnerable To Unpatched Linux Security Exploits

We say this because the Fraunhofer Institute for Communication (FKIE) in Germany recently performed test of 127 home routers, to probe them for their resistance to security threats. Of the routers the researchers tested, 91 percent of them were found to be running some version of embedded Linux, which isn’t surprising.
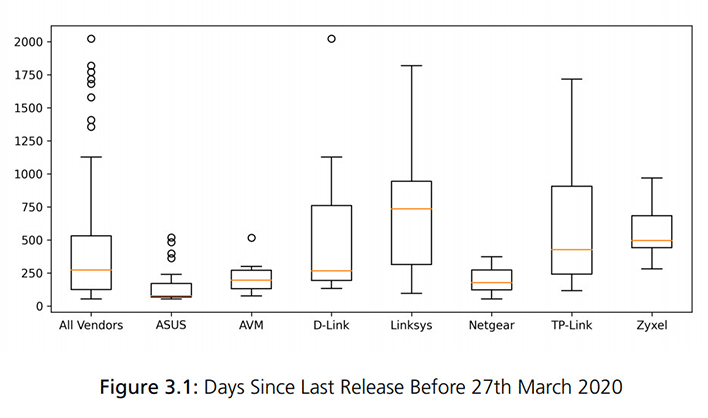
What was surprising, however, was that the researchers found that not a single router was free of security flaws. In fact, it was discovered that many of these routers were actually susceptible to hundreds of known security vulnerabilities. With respect to modern vulnerabilities, we all know that no device is absolutely perfect. Security vulnerabilities in networking products -- especially routers -- are found all the time, so it's critical that manufacturers put out frequent firmware updates and patches to at least stay somewhat on top of newly discovered exploits. It's incumbent upon router manufacturers to provide continuous maintenance updates on their products.

However, FKIE found that over 25 percent of the tested routers hadn't received a single security-related update in over a year (some as long as five years). And the problems don't stop there. "Some routers have easy crackable or even well-known passwords that cannot be changed by the user," wrote the FKIE researchers. "Most firmware images provide private cryptographic key material. This means, whatever they try to secure with a public-private crypto mechanism is not secure at all."
In conclusion, the researchers added:
"Many routers are powered by very old versions of Linux. Most devices are still powered with a 2.6 Linux kernel, which is no longer maintained for many years. This leads to a high number of critical and high severity CVEs affecting these devices."
You can find the full research report here (PDF). The bottom line, however, is that you should research OEMs before purchasing your next router, and see what their track record is like with respect to security updates and firmware upgrades. Don't let attractive pricing take your eye of the ball, as this is a piece of hardware that you will likely be keeping around and connecting your devices and home to the internet with for years.


