Intel Security Report Finds AMD Processors Twice As Vulnerable And Buggy
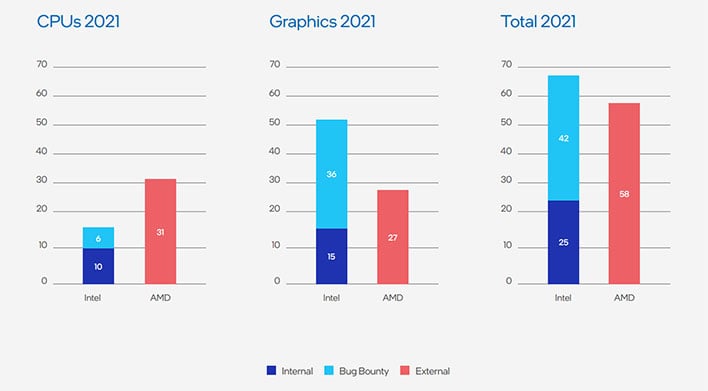
Intel has published its 2021 Product Security Report and in it the company suggests its processors are far less buggy than AMD's chips. The key section is on page 28 where Intel highlights having reported 16 CPU vulnerabilities last year, whereas AMD reported 31 CPU vulnerabilities in the same time period. What can we derive from that stat?
To be clear, Intel doesn't come right out and say its processors are more secure than its rivals chips. It does, however, strongly suggest as much with a bunch of stats and graphs. According to Intel, its own researchers discovered 10 of the 16 CPU vulnerabilities affecting its chips, while the other half dozen resulted from its bug bounty program (which it recently expanded with Project Circuit Breaker).
The picture isn't quite as rosy for Intel when shifting focus to graphics. In the same report, Intel points to 51 graphics vulnerabilities within its own chips, compared to 27 for AMD. If combining the two (CPU and GPU vulnerabilities), AMD comes out ahead with 58 total, versus 67 combined for Intel.
"Intel security research for 2021 accounts for 50 percent of the issues addressed and an additional 43 percent were reported through Intel's bug bounty program. In 2021, we addressed 226 vulnerabilities compared to 231 in 2020 and 236 in 2019," the report states.
The chip maker's main points are that it's striving for security transparency with these kinds of reports, and that its efforts to proactively seek out and mitigate security issues are paying off. But does any of this mean Intel's chips are more secure than AMD's CPUs? Not necessarily.
Some have called into the question what can truly be derived from comparing CVEs that have been fixed.
"Don't look at CVEs that were fixed. Look at CVEs that aren't fixed, and published errata. There are LOTS of errata, some that have existed for generations. Also bugs that exist that haven't been made public don't have CVEs, or errata. Making any declaration is pretty useless," Dr. Ian Cutress stated on Twitter.
The types of vulnerabilities and potential impact on customers and clients are what matter most when evaluating security. For example, when Spectre and Meltdown made waves a few years ago, it was found that the latter impacted Intel's chips the most. That's not to say AMD's processors are better than Intel's or vice versa, just that a level head is needed when looking at these kinds of reports.
Somewhat related, Intel's report highlights that the majority of CVEs for its chips were rated medium (65 percent) or 11 percent (low) in severity. Only 1 percent carried a critical designation, and 23 percent were rated high.
For anyone interested, Intel's 2021 Security Report (PDF) also ranks bug bounty researchers by payout awards and branches off in a few other directions.