Shocking Study Exposes Lax Security Of Online Stores Entrusted With Your Data

In a perfect world, online stores would treat your personal data with the most stringent security policies, taking extra precautions to make sure your details don't end up for sale on the dark web. And to be fair, some do (or at least come close). However, a new study reveals that many online stores are inexcusably careless with your data, even though they might mean well.
It's admittedly a self-serving study by Sansec, an ecommerce malware, vulnerability, and digital skimming detection service. Even so, the study is disturbing—Sansec found that one in nine online stores accidentally exposed private backups in unprotected public web folders.
"This mistake could have dire consequences. Online criminals are actively scanning for these backups, as they contain passwords and other sensitive information. Exposed secrets have been used to gain control of stores, extort merchants and intercept customer payments," Sansec says.
Stores are doing the right thing by maintaining backups, which they'll be glad to have in the event of a major hardware failure or even a ransomware attack. But the problem lies in how and where your personal data is stored.
According to the study, it's common practice for stores to utilize ad-hock backups during routine platform maintenance. That in and of itself isn't inherently bad, but it represents a common failure point.
"The problem, however, is that these backups often end up in a public folder. Perhaps the administrator intended to remove it after the maintenance, but forgot about it? Few people would admit it, but these mistakes are extremely common," Sansec states.
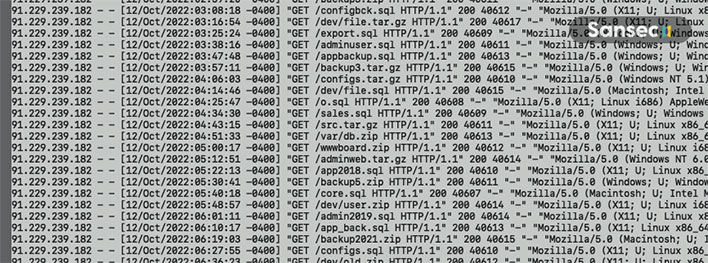
Example of a brute force probe for sensitive data (Source: Sansec)
In what the company claims is the first quantitative study to reveal the large scope of the problem, it found that more than 12 percent of stores risk being hacked and divulging customer details due to a "small human error." While Sansec didn't call out any online stores by name, it did say it looked at ecommerce sites of various sizes.
On 250 of the stores it looked at, it found archives (ZIP, SQL, and TAR files) in unprotected public web folders. Those backups contained database passwords, secret admin URLs and API keys, and all kinds of customer details.
"How easy is it for an attacker to discover such backups? Unfortunately, easier than you may think. We have observed automated attacks against online stores, where thousands of possible backup names are tried over the course of multiple weeks," Sansec says.
The study offers several tips for retailers to check for leaks and prevent future ones. Customers, however, are at the mercy of online sites to actually follow the tips and protect their data. Our advice is to follow smart computing practices, such as using strong and unique passwords, multi-factor authentication when available, and making use of temporary and/or virtual credit card numbers—some credit card companies offer this service, as does Privacy.com.

