Security Researchers Discover An Exploited Undetectable Windows Powershell Backdoor

The malware is distributed via a malicious Word document like so many other phishing attacks. The file is called “Apply Form.docm” and was first uploaded to VirusTotal on August 25, 2022. The M of the DOCM extension indicates that the Word Document includes macro code. As a rule, users should never open a document with macros without verifying who the document is from, that they are trusted, and that it is absolutely necessary—most users will never have reason to. Given how well known this attack vector is, it is especially concerning that none of the security vendors’ scanners picked up on it.
The document poses as a job application form and is related to an “alleged LinkedIn-based job application spearphishing lure.” In other words, it is used to target individuals who are likely to have access to highly sensitive data.
Its evasiveness is due in large part to code obfuscation. The researchers explain how the document instructs those who open the file to enable editing and then enable content. The enable content button allows the embedded macro to run, which places a file called updater.vbs into a fake folder located at “%appdata%\local\Microsoft\Windows\Update\” and also schedules a task to run this script.
Before the scheduled task runs, the macro also creates two PowerShell scripts from text hidden within the Word document. Script.ps1 gathers commands from the C2 server, which also assigns a unique victim ID. Temp.ps1 decodes the command and executes it using one of three processes.
The researchers spotted a weakness in how the victim IDs were assigned. The IDs are simply incremented sequentially, so the researchers note that their initial ID number of 70 likely indicates that there were 69 prior victims. This observation allowed the researchers to masquerade as these prior victims to the C2 server, then extract all the tailored commands it returned.
SafeBreach Labs found two thirds of the commands sought to exfiltrate running process lists from the target’s computer. Another 7% employed the whoami command to return local users alongside the process list. A small number of other commands sought to list files from common folders, remove files from public folders, or even parse all Active Directory users and Remote Desktop clients. The remaining 23% of commands were to simply sit idle.
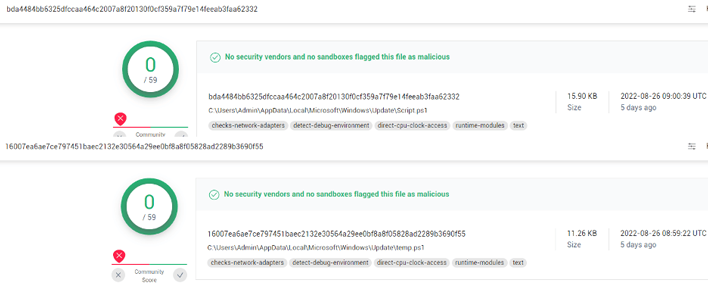
The fetching of commands and general obfuscation makes the attack very difficult to detect directly. To aid security vendors and other organizations, SafeBreach has published the following indicators of compromise (IOCs) which serve as signatures to aid in detection:
-
C2 server –
hxxp://45.89.125.189/put,hxxp://45.89.125.189/get— The C2 server is not active since September 5 2022 -
Apply Form.docm —
45f293b1b5a4aaec48ac943696302bac9c893867f1fc282e85ed8341dd2f0f50 -
Updater.vbs —
54ed729f7c495c7baa7c9e4e63f8cf496a8d8c89fc10da87f2b83d5151520514 -
Script.ps1 —
bda4484bb6325dfccaa464c2007a8f20130f0cf359a7f79e14feeab3faa62332 -
Temp.ps1 —
16007ea6ae7ce797451baec2132e30564a29ee0bf8a8f05828ad2289b3690f55