Regin Espionage Malware Discovered Targeting Communications, Energy And Airlines
Symantec made the unsettling announcement today that it has discovered sophisticated malware that has been operating successfully on and off since 2008. Named Regin, the malware launches in a series of stages and is designed to avoid detection at each stage. Symantec hasn’t identified the organization that created Regin, but says that its sophistication, its targets, and the amount of time that would be needed to create it suggest that a nation state is responsible.
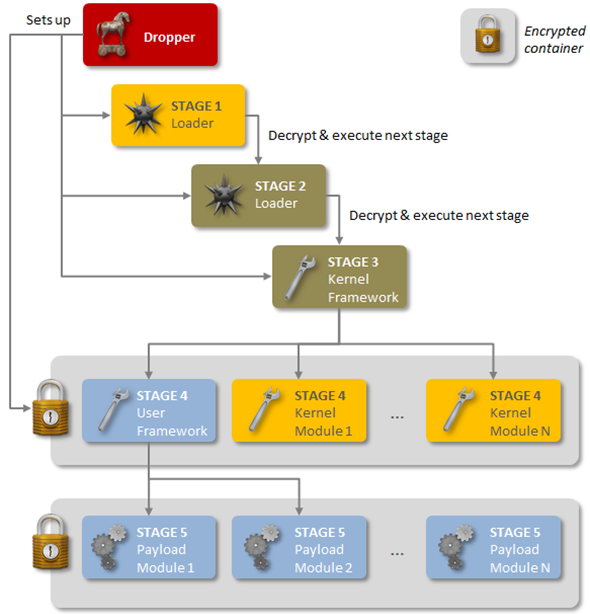
Image Credit: Symantec
Regin’s first stage is a Trojan. Once launched, the malware goes through several stages, each of which is encrypted. The payload is delivered in the fifth stage. Once complete, the malware can be used for spying on the target. Depending on the payload, it can let users steal passwords, hunt for deleted files, or control the mouse cursor.
So far, small businesses and private individuals have made up almost half the infections that Symantec has discovered, with another 28 percent of infections being telecoms companies. Airline, energy, and hospitality industries have also seen heavy Regin infections. According to Symantec, it appears that the malware provider designed Regin for spying on calls routed through these businesses. Russia and Saudi Arabia are the sites of the bulk of the Regin infections, but the malware has been discovered in multiple countries around the globe. In its white paper on the malware, Symantec points out that Regin first started attacks in 2008 and then seems to have been halted by the originator around 2011. It reappeared in 2013, with an updated design.

Image Credit: Symantec
Regin’s first stage is a Trojan. Once launched, the malware goes through several stages, each of which is encrypted. The payload is delivered in the fifth stage. Once complete, the malware can be used for spying on the target. Depending on the payload, it can let users steal passwords, hunt for deleted files, or control the mouse cursor.
So far, small businesses and private individuals have made up almost half the infections that Symantec has discovered, with another 28 percent of infections being telecoms companies. Airline, energy, and hospitality industries have also seen heavy Regin infections. According to Symantec, it appears that the malware provider designed Regin for spying on calls routed through these businesses. Russia and Saudi Arabia are the sites of the bulk of the Regin infections, but the malware has been discovered in multiple countries around the globe. In its white paper on the malware, Symantec points out that Regin first started attacks in 2008 and then seems to have been halted by the originator around 2011. It reappeared in 2013, with an updated design.

