Octo Banking Malware Threatens To Get Its Remote Control Tentacles Into Android Devices

In January of this year, the ThreatFabric team stumbled upon a post on a darknet forum wherein a member was asking for the Octo Android botnet. At that time, researchers were unclear if this was from a new family of malware or a rebrand of something seen in the past. Then in February, another member of the forum uncovered the owner and seller of the Octo botnet, known as "Architect." The researchers then correlated the "Architect" with other accounts, which helped to reveal similarities in the features of the Octo botnet and ExobotCompact.
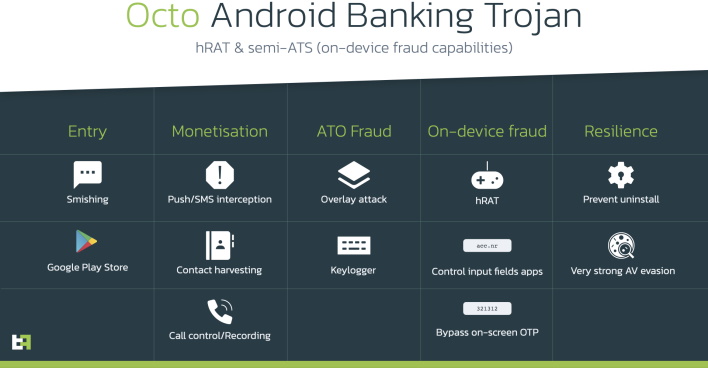
With these connections made, the ThreatFabric team began to pull together the capabilities of Octo/ExobotCompact that allowed it to stay "under the radar and perform on-device fraud (ODF)." This, concerningly, includes the lack of anti-detection and analysis techniques, but proprietary payload protections developed by the author. This comes in the form of a native library to "decrypt and load the malicious payload, which makes it hard to analyze and detect." Once running, the malware can harvest contacts, intercept messages and calls, perform keylogging, perform overlay attacks, and more, as shown in the above image.
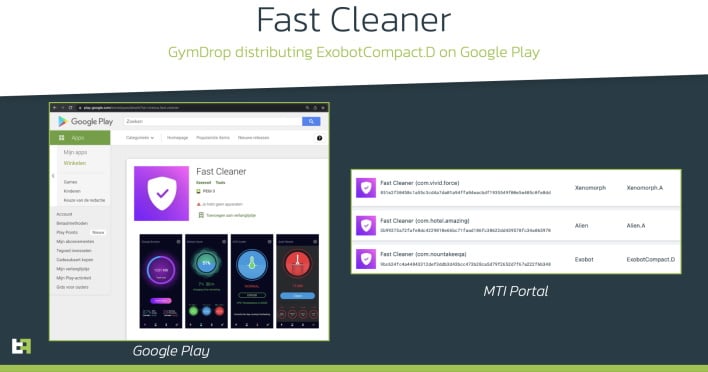
Since Octo is a for-rent banking trojan, ThreatFabric explains that it is used by several threat actors maintaining different campaigns around the world. Their distribution techniques include packaging Octo with apps on the Google Play Store with thousands of downloads or spoofing Google Play updates through malicious websites. Regardless of how Octo gets onto a device, it will certainly wreak havoc on an unsuspecting victim. But, to help prevent this, it is recommended that financial institutions "have strong client-side detection solution that can detect malware not only by signatures (ExobotCompact proves that it can be useless), but by its malicious behavior."
(Images and information courtesy of Threat Fabric)

