Mozilla To Enable This Controversial Security Feature In Firefox By Default

As far as Mozilla is concerned, its Firefox browser is becoming more secure by being the only one to enable encrypted DNS over HTTPS (DoH) by default for users in the United States. The gradual rollout has already begun and will continue over the new few weeks, so long as no major issues rear their ugly heads.
"Today, we know that unencrypted DNS is not only vulnerable to spying but is being exploited, and so we are helping the internet to make the shift to more secure alternatives. We do this by performing DNS lookups in an encrypted HTTPS connection. This helps hide your browsing history from attackers on the network, helps prevent data collection by third parties on the network that ties your computer to websites you visit," Mozilla explains.
Mozilla's contention is that DNS was designed decades ago, and when browsers perform DNS lookups for websites, including ones with HTTPS enabled, they're usually done without encryption. As a result, Mozilla points out that other devices along the way might collect a user's data, and that DNS lookups get sent to servers that can spy on a user's browsing history withing informing the user.
This is where DoH comes into play. By using HTTPS to exchange DNS packets, Mozilla says user's are ensured that no one can spy on their DNS requests. For a more in-depth breakdown of how it all works, check out Mozilla's cartoon intro to DoH.
So, what's the controversy? Last year, ZDNet posted an article citing several security experts, companies, and national entities all calling into question how effective DoH really is. One of the reasons is because DNS is not the only data point that ISPs use to track users.
DoH encrypts precisely zero data that is not already present in unencrypted form. As it stands, using DoH only provides *additional* leaks of data. SNI, IP addresses, OCSP and remaining HTTP connections still provide the rest. It is fake privacy in 2019.
— Bert Hubert 🇪🇺 (@PowerDNS_Bert) September 22, 2019
Software developer Bert Hubert went so far as to call DoH "fake privacy."
"DoH encrypts precisely zero data that is not already present in unencrypted form. As it stands, using DoH only provides *additional* leaks of data. SNI, IP addresses, OCSP and remaining HTTP connections still provide the rest. It is fake privacy in 2019," Hubert said on Twitter.
Another point raised is that when DoH is enabled, organizations are unable to use a DNS query's data to see if a user is trying to access a domain that is known to be malicious. According to a paper published by the SANS Institute, a cyber security training firm, "the unmitigated usage of encrypted DNS, particularly DNS over HTTPS, could allow attackers and insiders to bypass organization controls."
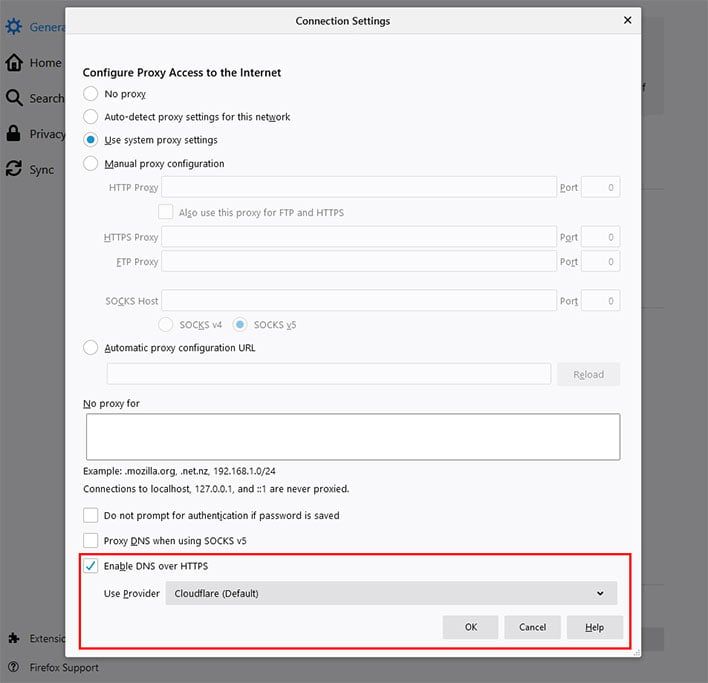
Nevertheless, Mozilla is forging ahead with DoH in Firefox for users in the US. When enabled, users can choose between Cloudflare and NextDNS, with Cloudflare being the default. You can find the option by going to Settings > General and scrolling down to Network Settings, then click the Settings button.
This is also where you can go to disable DoH if you're concerned about it (or enable it if you live outside the US).