DROWN Exploit Puts Millions Of OpenSSL Secured Web Sites At Risk For HTTPS Encryption Attacks
DROWN preys on servers that still openly support Secure Sockets Layer (SSLv2), even though modern servers have moved on to Transport Layer Security (TLS). Given that SSLv2 was developed in the 1990s, it’s long been considered outdated and insecure. However, some servers have still been configured to support SSLv2 for whatever reason, which leaves websites wide open to attacks. A server merely needs to have SSLv2 support enabled = to become vulnerable, which is when hackers utilizing DROWN move in for the kill.
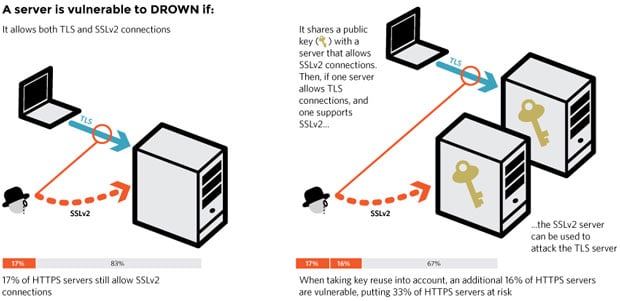
Researchers discovered that 17 percent of HTTPS servers are misconfigured to allow SSLv2 connections to occur — this is one attack vector. The second vector comes in the form of a certificate and private key being shared between a web server and an email server. The researchers write:
In this case, if the email server supports SSLv2 and the web server does not, an attacker can take advantage of the email server to break TLS connections to the web server. When taking key reuse into account, an additional 16% of HTTPS servers are vulnerable, putting 33% of HTTPS servers at risk.
Some popular sites are vulnerable to man-in-the-middle DROWNing attacks including Yahoo, flickr, Alibaba, Weibo and Daily Motion. So what exactly is at risk of being obtained by malicious parties attempting to DROWN a website? Well, the sky’s the limit according to the researchers:
Any communication between users and the server. This typically includes, but is not limited to, usernames and passwords, credit card numbers, emails, instant messages, and sensitive documents. Under some common scenarios, an attacker can also impersonate a secure website and intercept or change the content the user sees.
If your server users OpenSSL, it is recommended to upgrade to the most recent version of the cryptographic library. OpenSSL 1.0.1 users need to upgrade to 1.0.1s, while OpenSSL 1.0.2 users need to migrate to 1.0.2g. If you’re using Microsoft IIS Version 7.0 or above, SSLv2 should be disabled by default. Likewise, if you’re using Network Security Services version 3.13 or above, SSLv2 should also be disabled by default.
The big takeaway, however, is to keep your software updated and when possible, simply avoid enabling SSLv2 at all costs. For more on DROWN, be sure to check out this page which offers a thorough FAQ and a full technical paper [PDF].