Microsoft Azure Cosmos DB Database Security Flaw Exposed Client Data For Years

Researchers at a cybersecurity firm headquartered in Israel say they recently alerted Microsoft to a startling vulnerability in its Azure Cosmos DB database service. Multiple flaws could allow an attack to "gain complete unrestricted access" to accounts and databases of several thousand companies, including Fortune 500 outfits like Coca-Cola, Exxon-Mobil, Citrix, and more.
The researchers have dubbed the vulnerability #ChaosDB, noting that it consists of a series of flaws that effectively create a loophole for any user to access a customer's data. This flaw left more than 3,300 companies exposed to potential hacks, whereby a malicious actor (or anyone) could "download, delete, or manipulate" databases. They also would have read and write access to the underlying architecture of Cosmos DB.
Lots of companies use Cosmos DB to manage large blocks of data from around the world in real-time, offering a simple way to store data. It also processes millions of prescription transactions and manages customer order flows on e-commerce sites, highlighting why a potential exposure of this magnitude is so troubling.
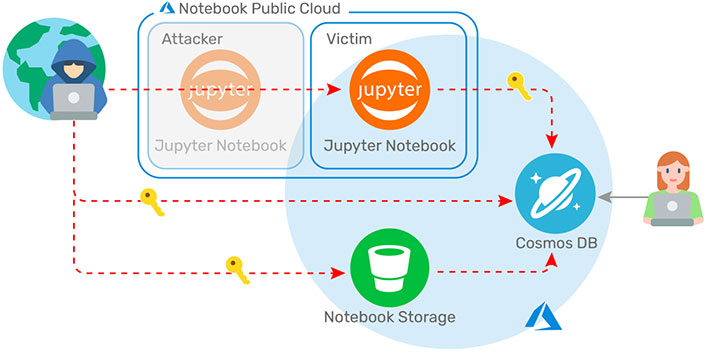
According to the researchers at Wiz, who discovered the series of flaws, the vulnerability had been around for a couple of years, when Microsoft added a feature called Jupyter Notebook to its Cosmos DB product. This lets customers visualize their data and create customized views. Then in February of this year, Microsoft automatically enabled it for all Cosmos DBs.
"A series of misconfigurations in the notebook feature opened up a new attack vector we were able to exploit. In short, the notebook container allowed for a privilege escalation into other customer notebooks," Wiz explains. "As a result, an attacker could gain access to customers’ Cosmos DB primary keys and other highly sensitive secrets such as the notebook blob storage access token."
After harvesting keys, the researchers were able to demonstrate how an attacker could gain full admin access to the data stored in any particular account. Not good.
That said, the researchers point out that customers can still be impacted because their primary keys were potentially exposed. So if a malicious actor was able to record the keys prior to Microsoft locking things down, they could still wreak havoc.
"Microsoft only emailed customers that were affected during our short (approximately weeklong) research period. However, we believe many more Cosmos DB customers may be at risk. The vulnerability has been exploitable for at least several months, possibly years," Wiz says.
Microsoft seemingly disagrees. In a statement provided to Bloomberg, Microsoft said it has found "no evidence of this technique being exploited by malicious actors," adding that it is "not aware of any customer data being accessed because of this vulnerability."