Snooping Kr00k Wi-Fi Security Flaw Affects Billions Of Devices Including iPhones, Androids, Raspberry Pi

The problem lies with Wi-Fi chips that were manufactured by Broadcom and Cypress Semiconductor, and Kr00k would allow anyone with the proper tools within close proximity to your Wi-Fi network to bypass WPA2 encryption.
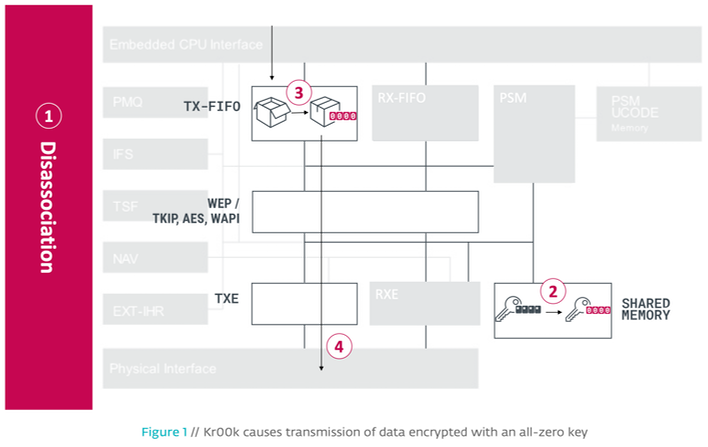
Kr00k takes advantage of a period of a time when a device disconnects from a network either when roaming from access point to access point, or when it is forced off in a suspicious manner. After the targeted device then reconnects to the network, it will transmit the previously unsent data (usually around a few kilobytes in size) encrypted with a key consisting of all zeros. This is a serious degradation in encryption security compared to a normal WPA2-encrypted session.
"Once a station’s WLAN session gets disassociated (1), the session key (TK) stored in the Wireless Network Interface Controller’s (WNIC) Wi-Fi chip is cleared in memory – set to zero (2)," writes the ESET team. "This is expected behavior, as no further data is supposed to be transmitted after the disassociation. However, we discovered that all data frames that were left in the chip’s Tx (transmit) buffer were transmitted (4) after being encrypted with this all-zero key (3)."
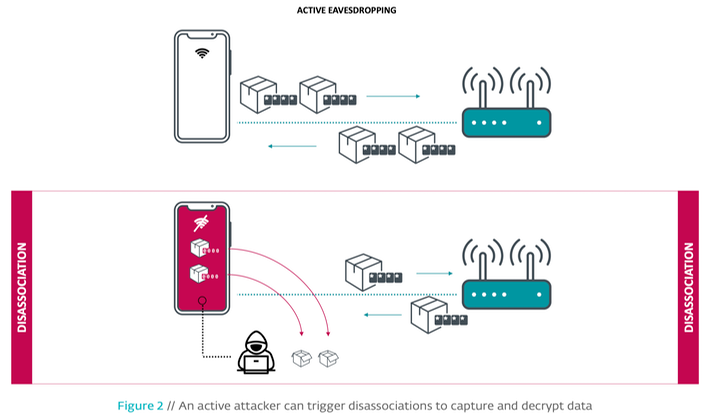
That few kilobytes of data can then be obtained by the hacker, which can easily decrypt it due to the all-zero encryption key. While that little bit of data might not sound like much, a hacker could potentially manually trigger multiple disconnects for a device to gather more data.
According to ESET, the following devices and access points/routers are affected:
- Amazon Echo 2nd gen
- Amazon Kindle 8th gen
- Apple iPad mini 2
- Apple iPhone 6, 6S, 8, XR
- Apple MacBook Air Retina 13-inch 2018
- Google Nexus 5
- Google Nexus 6
- Google Nexus 6S
- Raspberry Pi 3
- Samsung Galaxy S4 GT-I9505
- Samsung Galaxy S8
- Xiaomi Redmi 3S
- Asus RT-N12
- Huawei B612S-25d
- Huawei EchoLife HG8245H
- Huawei E5577Cs-321
Out of all the devices listed above, ESET us only able to confirm that Apple has patched Kr00k with its iOS 13.2/iPad OS 13.2 and macOS Catalina 10.15.1 operating system updates back in late October.
The fact that an attacker needs to be in close proximity to the victim to obtain data makes Kr00k less of a threat, but there’s still the potential for devices to leak passwords, username, and other sensitive data.

