Google Issues Another Emergency 0-Day Patch For Billions Of Chrome Installs, Update ASAP

Heads up to anyone who's running Google's Chrome browser—and a lot of people are, going by its massive market share—there's another actively-exploited zero-day vulnerability compromising its security. That's a bit of a big deal when you consider there are billions of Chrome installs. Fortunately, Google has pushed out an emergency patch.
As always when it comes to this sort of thing, Google is light on specifics to the extent of the zero-day. There's nothing nefarious about withholding such details, though. Quite the opposite, this is done to mitigate the risk as best as possible as scores of Chrome users get patched up. Otherwise, revealing details about the security hole would only make it easier for hackers to exploit it.
"Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed," Google explains.
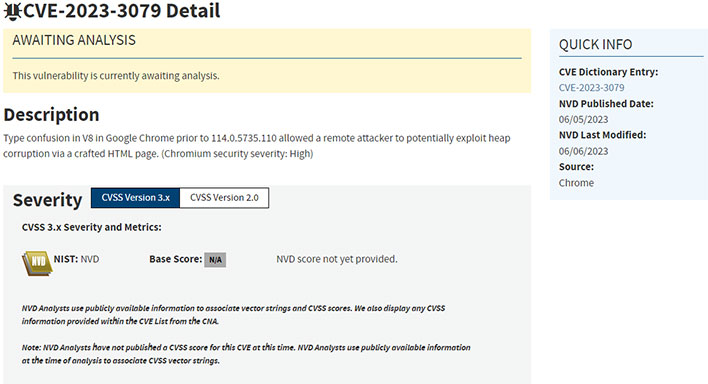
That said, we do know a few details. This particular flaw (CVE-2023-3079) is another "Type Confusion in V8", which is Chrome's JavaScript engine, and it carries a 'High' severity rating.
Clément Lecigne from Google's Threat Analysis Group discovered the flaw, for which it's known that an exploit "exists in the wild." Hence why it's imperative to update your Chrome browser to the latest release. Otherwise, you're basically a sitting duck.
The flaw exists in Chrome builds prior to 114.0.5735.110. It allows a "remote attacker to potentially exploit heap corruption via a crafted HTML page." This is the second V8 flaw Google has patched in Chrome this year, and the third zero-day (CVE-2023-2136 and CVE-2023-2033 being the other two).
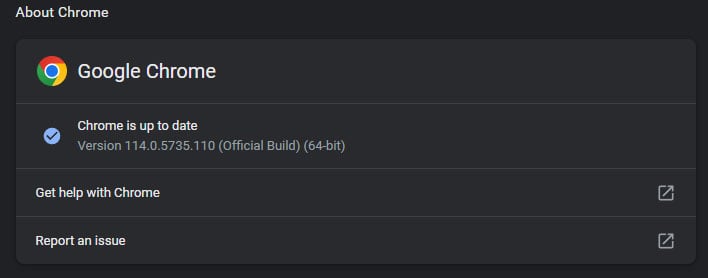
By default, Chrome downloads fetches updates on its own and prompts you to relaunch the browser to finish installing it (or will do it the next time you close and re-open Chrome). However, you can force the issue by clicking on the three vertical dots in the upper-right corner and selecting Help > About Google Chrome.
You'll be prompted to restart the browser. Chrome will reload any open tabs, though if you're working on anything in a CMS, be sure to save your work beforehand.
As for Microsoft's Edge browser, which is based on Chromium, we assume it's affected by the same zero-day vulnerability based on a recent support article update.
"Microsoft is aware of the recent exploits existing in the wild. We are actively working on releasing a security patch," Microsoft stated this week.
"While we get the security fix rolled out, it is worth highlighting that Microsoft Edge's enhanced security mode feature helps mitigate this vulnerability. You can opt-in into this security feature and have peace of mind that Microsoft Edge is protecting you against this exploit. After the security fix is released, make sure you still update your browser," Microsoft added.
As of this writing, the latest version of Edge in Windows is 114.0.1823.37, which was pushed out on June 2, 2023. It does not contain a fix for the aforementioned zero-day.