Cloudflare Successfully Foils Largest DDoS Attack Ever Recorded Amid Mirai Resurgence

The cybersecurity folks at Cloudflare have to be feeling like a million bucks right about now. Or make it a billion smackers. Either way, they are completely justified in reveling at staving off a massive distributed denial of service (DDOS) attack, the largest ever, in fact. It happened earlier this summer, only you never knew it, because of Cloudflare's efforts.
Perhaps the best part about this whole situation is that the largest attack effort ever recorded was automatically detected and mitigated, by Cloudflare's autonomous edge DDoS protection systems. These are powered by the firm's own home-grown software-defined denial of service daemon.
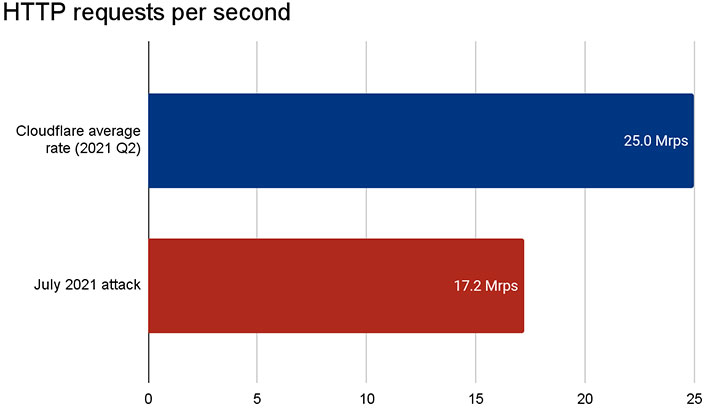
How large of an attack are we talking about? According to Cloudflare, its protections mitigated a DDoS attack that pinged 17.2 million requests per second.
"For perspective on how large this attack was: Cloudflare serves over 25 million HTTP requests per second on average. This refers to the average rate of legitimate traffic in 2021 Q2. So peaking at 17.2 million requests per second, this attack reached 68 percent of our Q2 average request per second rate of legitimate HTTP traffic," the security outfit states in a blog post.
As configured, a unique denial of service daemon runs in every server in each one of Cloudflare's data centers around the world, and each of those independently analyzes out-of-path traffic samples. This is the key to asynchronously scanning for DDoS attacks without sacrificing latency and reducing performance. In addition, the findings are shared among denial of service daemons. When an attack is detected, the systems generate a mitigation rule with a real-time signature matching the attack patterns.
"The rule is propagated to the most optimal location in the tech stack. As an example, a volumetric HTTP DDoS attack may be blocked at L4 inside the Linux iptables firewall instead of at L7 inside the L7 reverse proxy which runs in the user space," Cloudflare explains. "Mitigating lower in the stack, e.g. dropping the packets at L4 instead of responding with a 403 error page in L7, is more cost-efficient. It reduces our edge CPU consumption and intra-data center bandwidth utilization—thus helping us mitigate large attacks at scale without impacting performance."
According to Cloudflare, not only is this effective at automatically mitigating attacks that saturate 68 percent of its average per second rate, but even higher, before manual mitigation is required.
This particular attack is related to the resurgence of Mirai, a nasty botnet that has been wreaking havoc, and targeted a customer in the financial industry. It took just a few seconds for the botnet to ping the Cloudflare edge with over 330 million attack requests, with more than 20,000 bots located in 125 countries contributing to the malicious effort.
Cloudflare says this latest DDoS attack effort was nearly times the size of any other reported HTTP DDoS attack it has ever seen. It also notes that the attack and others like it have been observed in increasing frequency on its network over the past few weeks. Here's hoping Cloudflare continues to be successful in thwarting these attempts.