Alarming CASPER Attack Covertly Steals Data By Listening To Your PC's Internal Speaker

A new covert channel attack was discovered by the School of Cyber Security at Korea University in Seoul that can leak sensitive data from internal speakers in a computer to a nearby attacker's microphone housed in either a smartphone or laptop. Known as Casper, the attack leverages high frequency audio waves to transmit binary code or morse code to a microphone from up to 5 feet away, to attack critical system infrastructure that might be isolated from a computer network. The high frequency radio waves the attack implements are above the hearing range of the human ear, making it impossible to audibly locate the attack.
The researchers were able to test this attack method with a target system running Linux Ubuntu 20.04, and a Samsung Galaxy Z Flip 3 Android smartphone as the capture device. The phone was equipped with a basic recorder application utilizing a sample frequency of up to 20kHz to record morse code coming from the target machine. To convert text to morse code, the researchers set a bit length of 100ms and used a combination of 18kHz and 19kHz frequencies to emulate dots and dashes respectively. The phone was positioned 1.6 feet away from the target computer and was able to successfully decode the word "convert" that was sent from the target device.
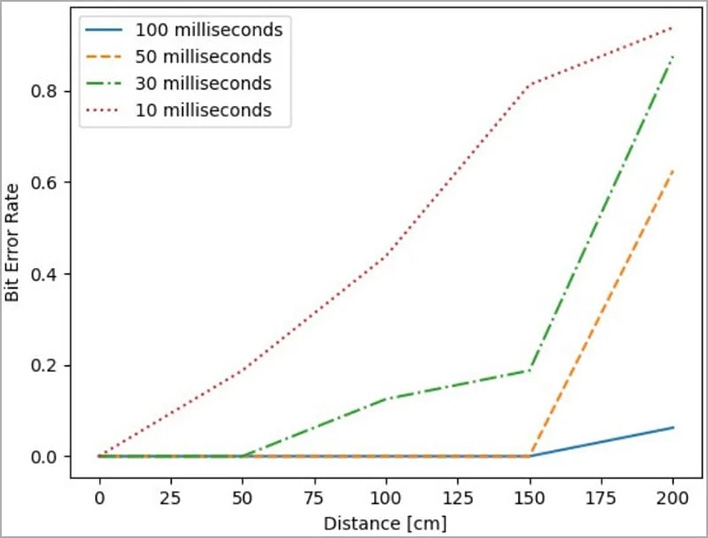
The researchers also produced another successful test involving binary data, utilizing a bit length of 50ms and a combination of 18kHz and 19kHz frequencies to send ones and zeros to the Samsung smartphone. Based on these two tests, the researchers realized that the bit length affects the error
rate of the transmissions, finding that a bit length of 50ms is 5 times more likely to get errors than 100ms
when transmitting at a distance of 200cm. The error rate gets even worse
at 30ms to 10ms, becoming roughly 40-50% worse compared to a 50ms sampling frequency.
This makes sense, because lower frequencies can transmit data at significantly longer ranges compared to higher frequencies, but it comes at the cost of bandwidth. As a result, it would be very important for an attacker to balance out the right frequency range for the given distance the signal has to travel, to get as much data from the target computer as quickly as possible. The researchers found that a maximum transfer speed of just 20bits/sec was achievable with a bit length of 50ms, at a distance of nearly 5 feet.
This attack strategy is designed specifically to attack critical system infrastructure that is isolated from any computer networks. The attacker would need to acquire physical access to the target machine and install a virus that can locate sensitive data and send it to the attacker over high frequency audio waves. The transmission rate for this system would be very small, so the attacker wouldn't be able to transmit a large amount of data. But it would still be very useful for grabbing smaller data types, such as codes, file names, and could be extremely effective at keylogging.
Technically, this attack method can also be used on normal computer speakers, but since most industrial computer equipment like rackmount servers aren't wired with external speakers, internal speakers are often the only speakers found on these machines. We don't know how the industry will fight back against this attack method, but the easiest way could be to simply remove any internal speakers used by the system.

