AT&T Customers Are Being Infected By A Massive Malware Botnet But User Data Is Allegedly Secure

In late October this year, researchers at 360 Netlab discovered a threat actor attacking Edgewater Networks' devices using the four-year-old CVE-2017-6079. This vulnerability, when exploited, could allow the attacker to execute commands via a hidden page embedded in the firmware dating back to 2006, according to the National Institute of Standards and Technology's database.
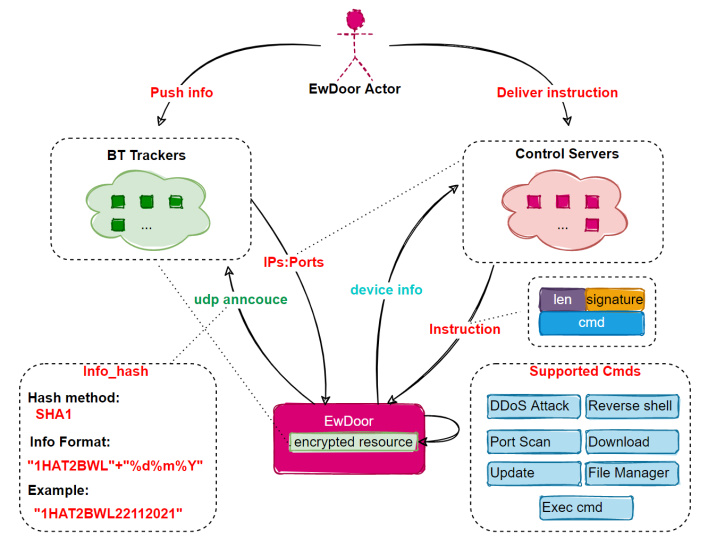
Subsequently, the researchers named this botnet EwDoor after "it's targeting of Edgewater producers and its Backdoor feature." The initial version of this network used a multi-command-and-control (C2) redundancy mechanism, allowing the researchers to register one of the C2 domains and gain some insights into EwDoor. They found that the 5,700 attacked devices are "EdgeMarc Enterprise Session Border Controllers" belonging to AT&T and geographically located within the United States.
Since that initial insight was gained, the researchers briefly lost sight of EwDoor, but found that there have been three known updates for the network that "can be summarized into 2 main categories of DDoS attacks and Backdoor." The thought is that with these capabilities, which also include "self-updating, port scanning, file management, reverse SHELL, and the execution of arbitrary commands," the threat actor wishes to deny service and gather sensitive information like call logs.
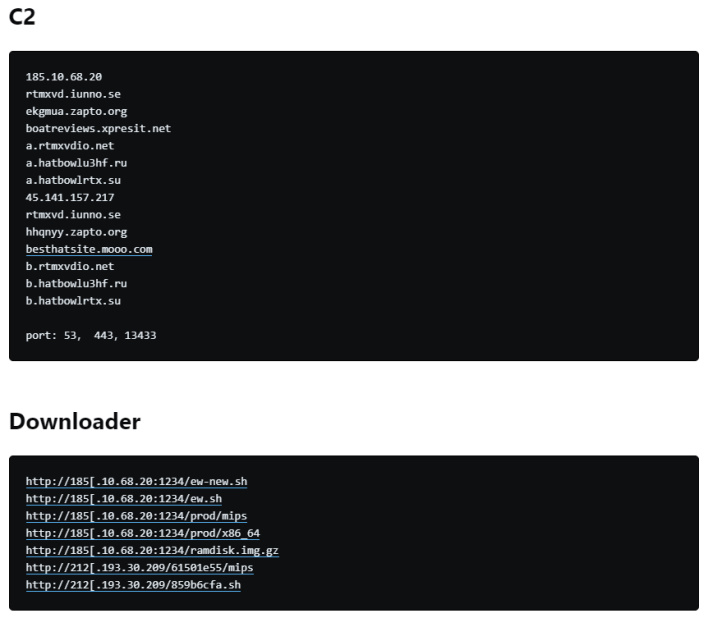
Interestingly, the team at 360 Netlab was able to deconstruct the code from EwDoor and found some of the C2 domains and the locations for the downloaded files. Though these have likely changed since the research was published, it shows that the threat actor's efforts to obfuscate their work had flaws.
In any event, AT&T spoke with BleepingComputer and stated that there was "no evidence of customers' data being accessed as a result of these attacks." Specifically, AT&T previously identified this issue, and the company has "taken steps to mitigate it and continue[s] to investigate." Despite this reassurance, it is still concerning that something like this could happen, especially considering the crux of this attack is a highly dangerous four-year-old vulnerability.

