AMD Issues BIOS Fixes For Several High Severity Zen Exploits, Update ASAP
AMD has just published the details of four new vulnerabilities affecting Zen-based CPUs. Not every Ryzen or EPYC chip is affected by all four exploits, but every AMD Zen processor is vulnerable to at least one. These exploits are pretty serious—each one allows attackers a method to spuriously update SPI ROM, installing malware into your motherboard.
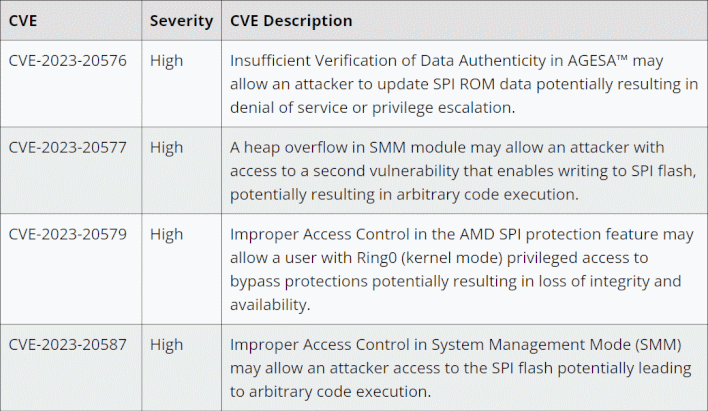
As far as we can tell, these flaws all require either administrative privileges or physical access, so there's no need to fly into a panic if you're just a regular user—just update your firmware as soon as you can. Of course, anyone administrating Ryzen or EPYC machines for business or government will definitely want to leap into action and get the patches, pronto.
Matthew over at Tom's Hardware did the legwork and figured out that Socket AM5 platforms and later Socket AM4 platforms (500 series chipsets) should have the requisite updates available as long as you're using a Ryzen 3000 or 5000-series processor. Folks using Cezanne ("G" chips on AM4) appear to be up a creek. You can head to AMD's disclosure page to see what AGESA version you need to be protected with your specific CPU.

