Vulnerability Discovered in Skyrim, Fallout 3, Oblivion and Other Bethesda Software Titles
In the world of software, it's not uncommon to learn of a program that's implemented vulnerable code for over a decade (Java, anyone?), but where gaming's concerned, that's another story. According to a security researcher simply going by "Joe", one such vulnerability has made Bethesda its home. Clearly the sort of guest that overstays their welcome, this vulnerability has appeared in the company's titles dating back to 2002, with Morrowind.
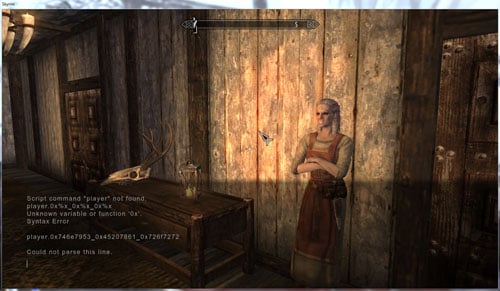
Exploiting the vulnerability is a matter of loading up the in-game console and writing out some simple hex code to alter some memory addresses. An example is with: "0x%x_0x%x_0x%x". When executed, the action skips a function due to how the calls are implemented, and shortly after, the game crashes. Joe proved this to happen with Skyrim, Morrowind and Fallout 3.
Unlike most vulnerabilities with software like Flash or Java, this one is about as tame as it gets. All of the confirmed vulnerable games are offline-only, so an attack over the Internet isn't going to happen except by bizarre means (eg: distributing malware that seeks out this vulnerability, which would be exceptionally silly). If Bethesda's games for some reason required administrator rights to operate, then the security risk could increase, but at this point it seems unlikely that any real harm could be done outside of annoying the absolute heck out of a gamer.
For purposes outside of exploits, it also seems unlikely that this vulnerability would benefit modders or game trainers (trainers being applications that live-edit memory addresses to affect the game), since those have already existed for a while. At best, this is just something to laugh at. That is, unless this bug also happens to make it through to The Elder Scrolls Online. As any MMO gamer knows, there's always those select few out there who haven't grown bored of telling people to Alt+F4 their clients. Perhaps soon we'll be saying, "Dude, you can fix it with 0x%x".