Severity Of Apple iOS “Masque Attack” Vulnerability Prompts Warning From US Government
On Monday, mobile security researchers at FireEye reported on the discovery that an iOS app installed using enterprise/ad-hoc provisioning would be able to replace genuine apps installed on a user’s phone. Dubbed the “Masque Attack” vulnerability, the US government has issued an additional warning today for Apple users.
“A technique labeled “Masque Attack” allows an attacker to substitute malware for a legitimate iOS app under a limited set of circumstances,” warned the US Computer Emergency Readiness Team in a post.
The post goes on to describe the attack as a technique that “takes advantage of a security weakness that allows an untrusted app—with the same “bundle identifier” as that of a legitimate app—to replace the legitimate app on an affected device, while keeping all of the user’s data. This vulnerability exists because iOS does not enforce matching certificates for apps with the same bundle identifier.”

If successful, the Masque Attack would give hackers access to a user's sensitive information from local data caches. In addition, hackers would also be able to perform background monitoring of the infected device, and obtain root privileges.
The government went on to offer advice for iPhone and iPad users to avoid the “Masque Attack:”
“A technique labeled “Masque Attack” allows an attacker to substitute malware for a legitimate iOS app under a limited set of circumstances,” warned the US Computer Emergency Readiness Team in a post.
The post goes on to describe the attack as a technique that “takes advantage of a security weakness that allows an untrusted app—with the same “bundle identifier” as that of a legitimate app—to replace the legitimate app on an affected device, while keeping all of the user’s data. This vulnerability exists because iOS does not enforce matching certificates for apps with the same bundle identifier.”


The government went on to offer advice for iPhone and iPad users to avoid the “Masque Attack:”
- Don’t install apps from sources other than Apple’s official App Store or your own organization.
- Don’t click “Install” from a third-party pop-up when viewing a web page.
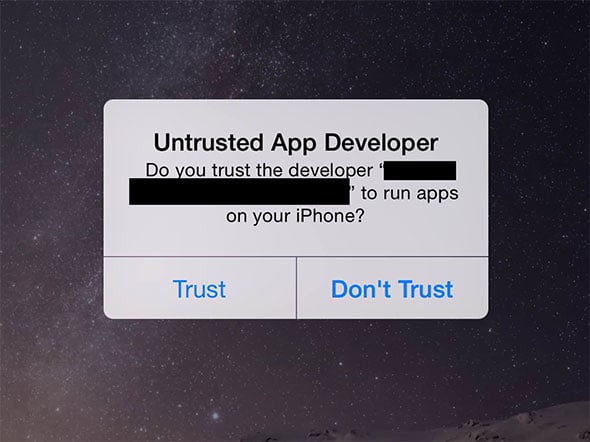
- When opening an app, if iOS shows an “Untrusted App Developer” alert, click on “Don’t Trust” and uninstall the app immediately.

