Waiter, There's Malware in My Soup!
October might officially be National Cyber Security Awareness Month, but based on the online security reports that have come out this July, it appears that Cyber Security Awareness is actually being promoted a few months early this year. First McAfee released its report on the lack of security measures being taken by small and medium businesses in the U.S. and Canada, and now security company, Sophos has just released its extensive snapshot of the state of worldwide, online security for the first half of 2008 with its Security Threat Report.
Based on the information collected by SophosLabs--which included receiving "approximately 20,000 new samples of suspect software every single day"--Sophos crunched the numbers on online security risks and came up with some pretty scary statistics, including the following:
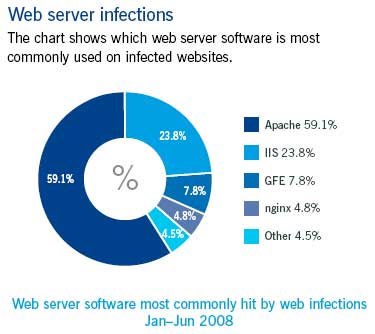
The report explains that "one of the reasons the web is so popular with attackers is that innocent sites can be compromised and used to infect large numbers of victims." These attacks target not only visitors to the sites, but often target the sites themselves via SQL injection attacks. Earlier this year the RIAA's site was hacked via SQL injection, as was Kaspersky's Malaysian site only a few days ago. More than half of the affected Web server software during the first half of 2008 were Apache servers.
Curiously, the percentage of malicious e-mail attachments is way down from this time last year. For the first half of 2007, Sophos reports that 1 out of every 332 e-mails contained a malicious attachment of some kind. For the first half of this year, that ratio is down to only one out of every 2,500. Sophos warns, however, that one should not assume that e-mail is necessarily safer; malicious e-mails are now just using more sophisticated techniques, such as linking to infected Websites, targeted malware (including spear-phishing), and backscatter spam. Spam is frequently the doorway to malware, and Sophos states that "only one in 28 emails is legitimate."
Microsoft Windows is the most prolific platform and therefore is the most frequently targeted for malware. But Sophos is seeing a growing trend of malware targeted at other platforms, such as the Mac OS, Linux OS, the iPhone, cell phones, and even social-networking sites. As users are less accustomed to encountering malware on these other platforms, they are far less likely to takea proactive approach to protect themselves from potential malicious attacks.
The stakes are high; much of the malware is designed to gain access to data and resources that enable cyber criminals to generate income from illegal activity such as identify theft and DOS attacks. Our coverage here only skims the surface of the depth that the report covers--follow the link below to see the full report (requires free registration).
Based on the information collected by SophosLabs--which included receiving "approximately 20,000 new samples of suspect software every single day"--Sophos crunched the numbers on online security risks and came up with some pretty scary statistics, including the following:
- A newly infected Webpage is discovered every five seconds
- A new spam-related Webpage is discovered every 20 seconds
- There are currently over 11 million different malware threats in existence
- Presently, the biggest malware threat is from SQL injection attacks against Websites
- The top host for malware is Blogspot.com
The report explains that "one of the reasons the web is so popular with attackers is that innocent sites can be compromised and used to infect large numbers of victims." These attacks target not only visitors to the sites, but often target the sites themselves via SQL injection attacks. Earlier this year the RIAA's site was hacked via SQL injection, as was Kaspersky's Malaysian site only a few days ago. More than half of the affected Web server software during the first half of 2008 were Apache servers.
 |
| Credit: Sophos |
Microsoft Windows is the most prolific platform and therefore is the most frequently targeted for malware. But Sophos is seeing a growing trend of malware targeted at other platforms, such as the Mac OS, Linux OS, the iPhone, cell phones, and even social-networking sites. As users are less accustomed to encountering malware on these other platforms, they are far less likely to takea proactive approach to protect themselves from potential malicious attacks.
The stakes are high; much of the malware is designed to gain access to data and resources that enable cyber criminals to generate income from illegal activity such as identify theft and DOS attacks. Our coverage here only skims the surface of the depth that the report covers--follow the link below to see the full report (requires free registration).

